Mercutio
Fatwah on Western Digital
Has anyone ever put together an Amazon EC2 instance? The pricing estimator is a little overwhelming.
Has anyone ever put together an Amazon EC2 instance? The pricing estimator is a little overwhelming.
Windows is, as usual, a requirement for what I'm deploying.
There's a data center not all that far from where I live. I'm contemplating just renting 2U of space for $50/month. I think I could stick a couple boxes in that and call it a cloud.
If a server needs a reboot will you have to drive over there?
Thanks. I didn't know that existed. We use expensives Raritan KVM switches with the Ethernet KVM modules. There's no power control module with it. It's significantly more expensive than the Lantronix gear you linked. I'll include this in my proposal.Lantronix Spider Duo with Power Control Module. I'm loving these things, now.
Of course, If I just stick a $100 Firewall appliance between my server and the internet, I also lose out on all the nifty management stuff the hosting service is supposed to provide me. And I'd have to worry about the damned thing needing reboots, which seems to be what happens with every SOHO router/firewall product that costs less than a small fortune.
If I build a VM to be a firewall and VPN end point I'll be making much more efficient use of my resources, but that seems like it would be a really clunky configuration to troubleshoot.
Of course, If I just stick a $100 Firewall appliance between my server and the internet, I also lose out on all the nifty management stuff the hosting service is supposed to provide me. And I'd have to worry about the damned thing needing reboots, which seems to be what happens with every SOHO router/firewall product that costs less than a small fortune.
If I build a VM to be a firewall and VPN end point I'll be making much more efficient use of my resources, but that seems like it would be a really clunky configuration to troubleshoot.
If you end up doing that, let me know how it works. I've been thinking of the same for quite a while, but would want to map a physical NIC directly to that VM for the red interface. Of course, you won't need to worry about that if the only machine inside the firewall is the ESXi box.
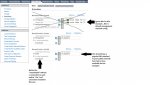
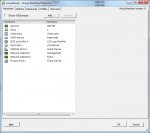
I'm playing with the setup now using a m0n0wall appliance I found online. vSwitches are something I've never messed and I'm more than a little concerned that I'm going to wind up with a system I can't interact with except from the console.
Thanks for the thorough reply, too!
Can I use the power control unit alone or do I have to use it in combo with the Lantronix Spider Duo? I have servers that already have KVM over IP, but which probably cannot be started by the dedicated IPMI port. I'm looking for a solution.Lantronix Spider Duo with Power Control Module. I'm loving these things, now.
